Nowadays .zip can denote a file or web page. That's confusing, at the very least, but also potentially downright dangerous.
Google is offering a new .zip web domain for users who want people to know they’re “fast, efficient, and ready to move.” It sounds mostly okay on paper, but due to the similarities between this domain and a popular zipped file format, there are concerns that this could become one of the easiest ways to dupe web-goers into downloading dodgy files.
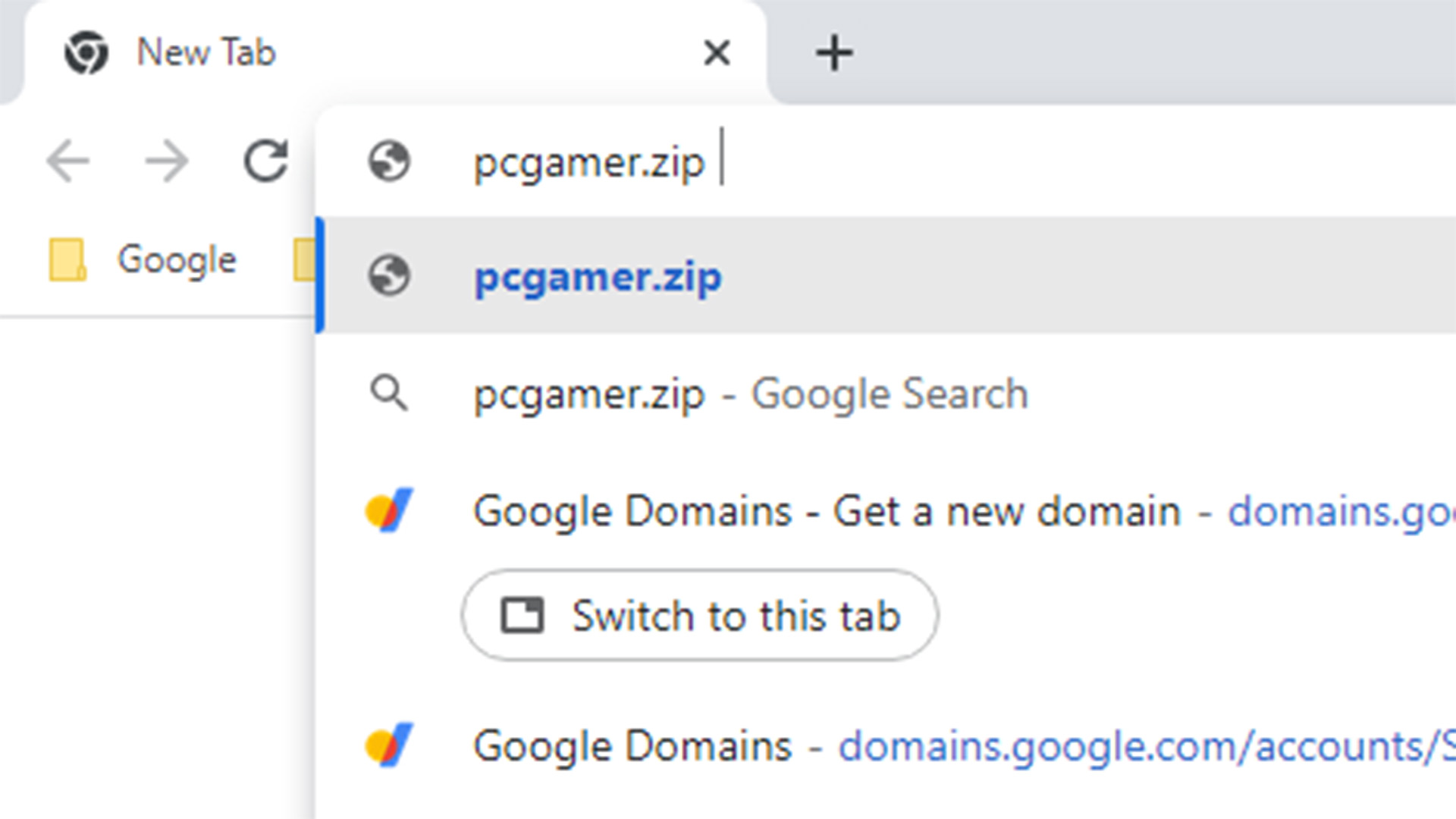
You can see why there have been concerns about the new .zip top level domain (TLD). Say you’re looking to download the CPU-Z software, you’d expect to land on the CPUID website at the URL: www.cpuid.com/downloads/cpu-z/cpu-z.2.05-en.zip.
What Google’s new .zip TLD will allow for are links that look very similar but are incredibly dangerous dupes. For example, and this link goes nowhere but there’s still no need to try it: www.cpuid.com/downloads/cpu-z∕@cpu-z.2.05-en.zip.
Most web-savvy users would probably notice the rogue @ in there and think twice before clicking on that URL, but you might not notice the Unicode character U+2215, which tries to masquerade as a forward slash. Cheeky.
As security researcher bobbyr points out in their Medium blog post, most modern browsers will disregard the information before the @ and only listen to the hostname following it. That means if you were to put in https://google.com@bing.com, most browsers would direct you to bing.com. If you were to add forward slashes into the URL before the @, you’d actually see the reverse happen: https://google.com/search@bing.com will take you to Google.
That’s where unicode characters U+2215 and U+2044 come in. These look a lot like forward slashes, but they’re not. And they’re supported in hostnames. That means you could create a fake URL that appears pretty genuine and which could send a user to a dodgy .zip url pretending to be a legitimate download. That domain could then host an actual .zip file with just about anything in it, including malware.
It’s kinda convoluted , but you can see the potential issue here, especially if someone’s not particularly internet savvy or in a rush.
.zip top level domains were a colossal mistake. pic.twitter.com/gqlEJEWLgGMay 12, 2023
Regarding the .zip domains I complained about – I think it’s dumb and unnecessarily creates confusion and will leave to various minor phishing schemes/tricks/address-confusion attacks… but it’s just going to get forced into being another TLD. It just feels uniquely unneeded.May 12, 2023
Not everyone agrees that this represents a new breed of phishing attack, however. Another Microsoft employee, and the creator of HaveIBeenPwned, Troy Hunt, suggests there’s nothing new here to worry about.
This is interesting reading regarding the .zip TLD. However, it’s of near zero consequence to phishing attacks, read it first then I’ll explain: https://t.co/RoN3L2m61oMay 17, 2023
The problem with the analysis in the blog post is that it asserts the new TLD can mislead people *on close inspection*. What new problem does this introduce that isn’t already present by changing the domain to one that sounds feasible?May 17, 2023
Hunt goes back to the argument that, ultimately, humans are “bad at URLs and TLDs don’t matter.” They suggest that most people have no idea when they’re presented with a deliberately deceptive address, whether the file looks like a .zip file or not.
“Most people have no idea when a feasible *looking* URL is completely wrong,” Hunt says.
(Image credit: Future)
Best gaming PC: The top pre-built machines from the pros
Best gaming laptop: Perfect notebooks for mobile gaming
But the key thing is that this isn’t really so much an issue for security researchers. They’ll almost certainly catch it. The issue are the less tech savvy internet users out there—.zip has become so synonymous with a file format, it does feel unnecessarily confusing to make it into a web domain, too.
The guidance to help users avoid .zip phishing attacks laid out in the Medium blog post is absolutely valid. You should keep an eye out for false characters in URLs, domains with @ symbols followed by .zip files, and to be careful when downloading files sent by unknown recipients.
In fact, that last one is really the best advice out there for avoiding getting phished. Scams pretending to be from known companies, services, or even people you know are some of the most dangerous.
You don’t need me to tell you this, but always be wary of what links you’re clicking on.



